INCIDENT RESPONSE
AI-driven e-mail incident response
protects your employees!
Enhance your security measures with our advanced Incident Response solution.
Uncover and eliminate historical phishing attacks effortlessly.
OVERVIEW
Incident
Response
Equip your team with a seamlessly integrated plugin that encourages prompt reporting of suspicious emails.
Gain an edge over emerging threats with real-time alerts, keeping you abreast of potential zero-day attacks.
Elevate your security posture and effortlessly navigate the evolving threat landscape.

Orchestrated Suspicious
Email Analysis
Full-automated
Real-time Inbox
Action
Investigation and
Migration
Fully Compatible
Reporter Add-in
Seamless Integration
with Log
Coleration Sources
FEATURES
E-mail Header
Analyze
Phishup technology analyzes email headers with DMARC, DKIM, SPF etc. checks to verify the authenticity of incoming messages. This process helps to identify and block fraudulent emails, reducing the risk of phishing attacks by ensuring that only legitimate messages from verified senders are delivered to users’ inboxes.
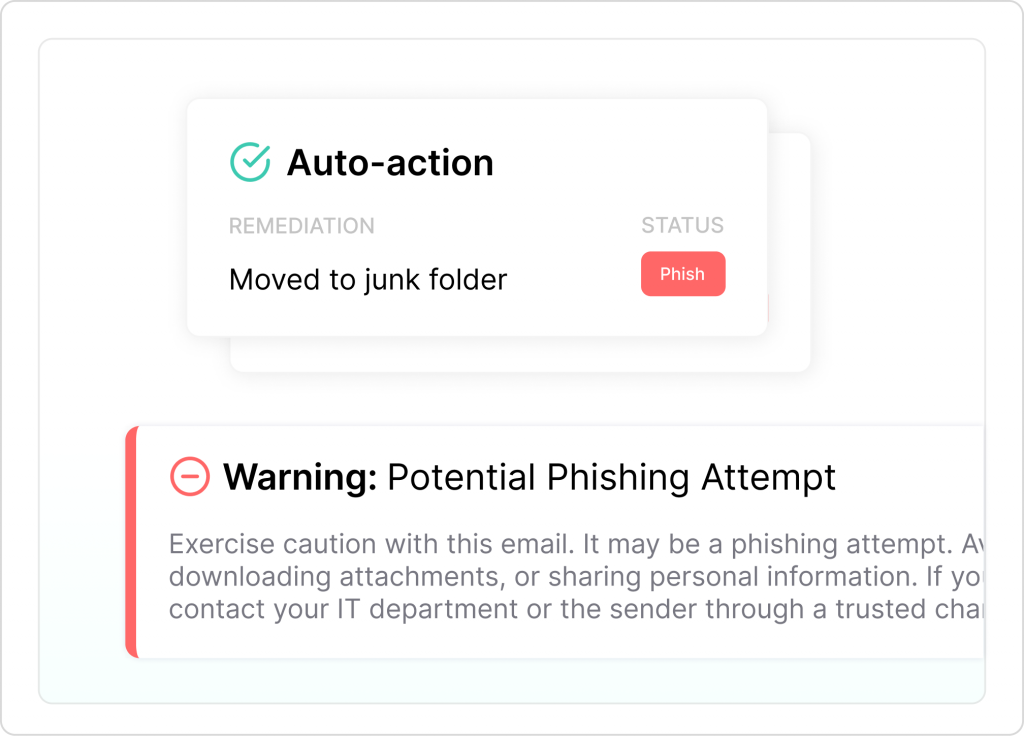
Immediate Actions Against to Inbound E-mail Attacks
This tool enables you to automatically delete every copy of the harmful email from users’ inboxes. Additionally, with automatic remediation, any emails containing dangerous links or attachments are identified and removed from users’ mailboxes after they’ve been delivered, ensuring enhanced protection with minimal manual effort.
Automate Your Incident Response Process Completely
Phishup technology analyzes email headers with DMARC, DKIM, SPF etc. checks to verify the authenticity of incoming messages. This process helps to identify and block fraudulent emails, reducing the risk of phishing attacks by ensuring that only legitimate messages from verified senders are delivered to users’ inboxes.

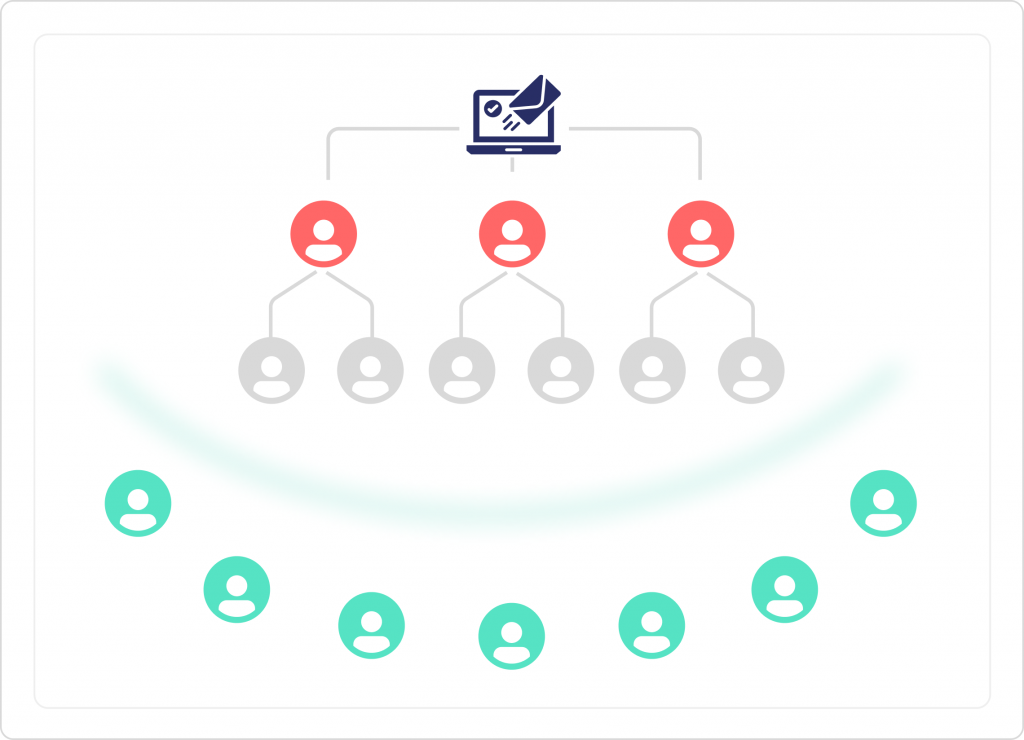
Take Precautions Against New Attacks
The Incident Response tool allows you to identify users who have clicked on a malicious link and automatically takes additional measures to limit the spread of the attack. By detecting employees who have clicked on these links, we can provide them with training to help prevent future incidents.
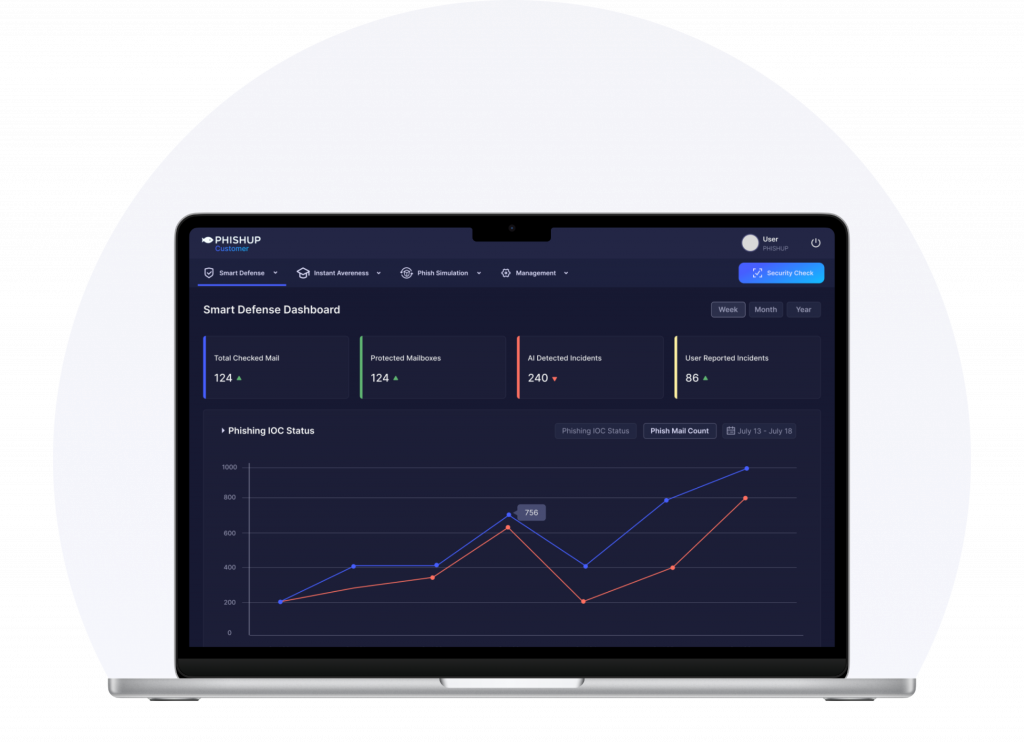
Take Detailed Insight & Take Protection
The Incident Response tool has powerful analytics that help you detect anomalies in emails already in your users’ inboxes. By using data from potential incidents created by you or other Phishup customers, as well as current threats identified by Phishup intelligence, you can prioritize and uncover new threats. This insight enables your team to identify otherwise unnoticed threats.
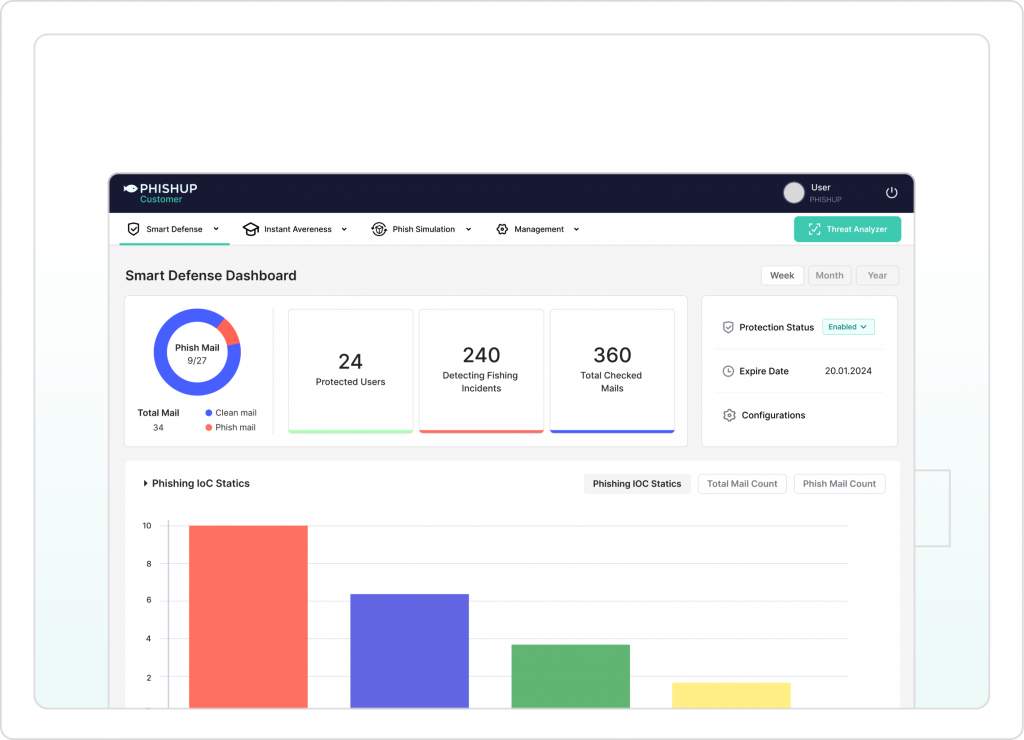
Multiple & Easy Integrations
Phishup seamlessly integrates with a wide range of platforms, making it simple to incorporate our solutions into your existing security infrastructure. Whether you’re using SIEM, SOAR, XDR, or other tools, Phishup offers easy integration options to enhance your threat detection and response capabilities.
- Microsoft 365
- Google Workspace
- Microsoft Exchange
- Forti Sandbox
- IBM QRadar
- Power BI
- Cortex XSOAR
- Check Point Quantum
FAQ
Frequently Asked Questions!
Take the first step to start protecting your employees now.
Does Phishup allow performing retrospective remediation?
Yes, it does. With the Retro Scan & Remediation features, Phishup enables retrospective remediation, allowing you to address and resolve past threats effectively.
Where is the collected data stored, and on which cloud server is it kept?
Your data is securely stored on cloud servers that comply with the requirements of the Turkish Personal Data Protection Law (KVKK). These servers are carefully selected to ensure they meet the highest standards of data protection and privacy.
Does Phishup offer reporting and analytics for incident response activities?
Absolutely. Phishup provides detailed reporting and analytics for all incident response activities.
Does the Incident Response feature allow viewing the actions detected and taken by AI?
Yes, it does. The Incident Response feature provides detailed visibility into the threats detected by AI and the corresponding actions taken, ensuring transparency and efficiency in your security operations.
Related Blogs

-
- Posted by Phishup

-
- Posted by Phishup
LET'S MEET
Get Free Demo Now!
Take the first step to start protecting your employees now.